In this post, you find out how DNSSEC and DANE cooperate, and learn how to set up DANE TLSA DNS records.
DNSSEC (DNS Security Extensions)
The domain name system (DNS) is the phone book of the Internet: it tells computers where to send and retrieve information. Unfortunately, it also accepts any address given to it, no questions asked.
DNSSEC adds a security layer to this phonebook. It uses digital signatures to make sure the information in the phonebook can be trusted and hasn’t been tampered with. It’s like putting a lock on the phonebook to prevent DNS spoofing.
DNSSEC can be enabled with your DNS provider if they support it.
DANE (DNS-based Authentication of Named Entities)
DANE used the DNS infrastructure to store details about the security of a service, such as the public key (fingerprint) of a certificate. These details act as a special seal of approval, ensuring that when your computer talks to this service, it’s real and it’s safe. DANE uses the TLSA (Transport Layer Security Authentication) record type, which allows users to verify the security details from a service (such as a web or mail server) by querying the DNS for its information.
DANE relies on DNSSEC and only works when DNSSEC is enabled.
Implementation of DANE
You can implement DANE with a TLSA record at your DNS hosting provider:
_port._protocol.yourdomain.comINTLSAusage-selector-matching certificate-fingerprint
For example, on port 443 (your web server):
_443._tcp.yourdomain.comINTLSA2 1 1 0B9FA5A59EED...(Root certificate)_443._tcp.yourdomain.comINTLSA3 1 1 0D073B9B73B4...(Host certificate)- 3:
usage - 1:
selector - 1:
Matching-Type
- 3:
The certificate usage type can be one of the following:
- 0: PKIX-TA (Trust Anchor)
- 1: PKIX-EE (End Entity)
- 2: DANE-TA (Trust Anchor Assertion: Intermediate / Root certificate)
- 3: DANE-EE (End Entity Assertion: Host certificate / Server certificate such as yourdomain.com)
The selector specifies how the certificate is presented:
- 0: Full certificate (not recommended)
- 1: SubjectPublicKeyInfo (recommended)
The Matching-Type specifies how the certificate association is verified:
- 0: No hash used (not recommended)
- 1: SHA-256 hash (recommended)
- 2: SHA-512 hash (not recommended / less supported)
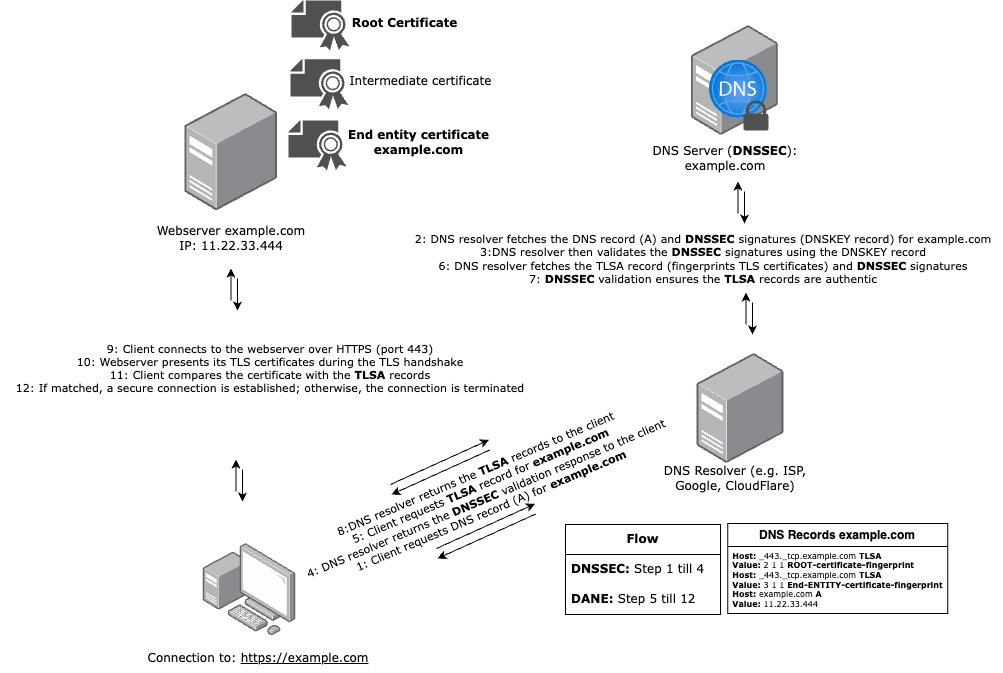
DNSSEC and DANE on a webserver
By combining DNSSEC and DANE, the integrity and authenticity of both the DNS responses and the TLS certificates are ensured, providing a robust mechanism to prevent man-in-the-middle attacks and improving overall webserver trust.
The flow of DNSSEC and DANE on a webserver
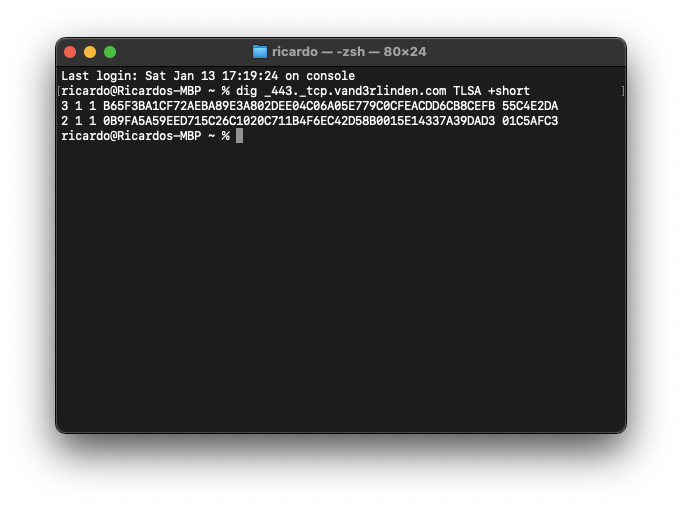
Example for this site, TLSA records:
Verify DANE TLSA records:
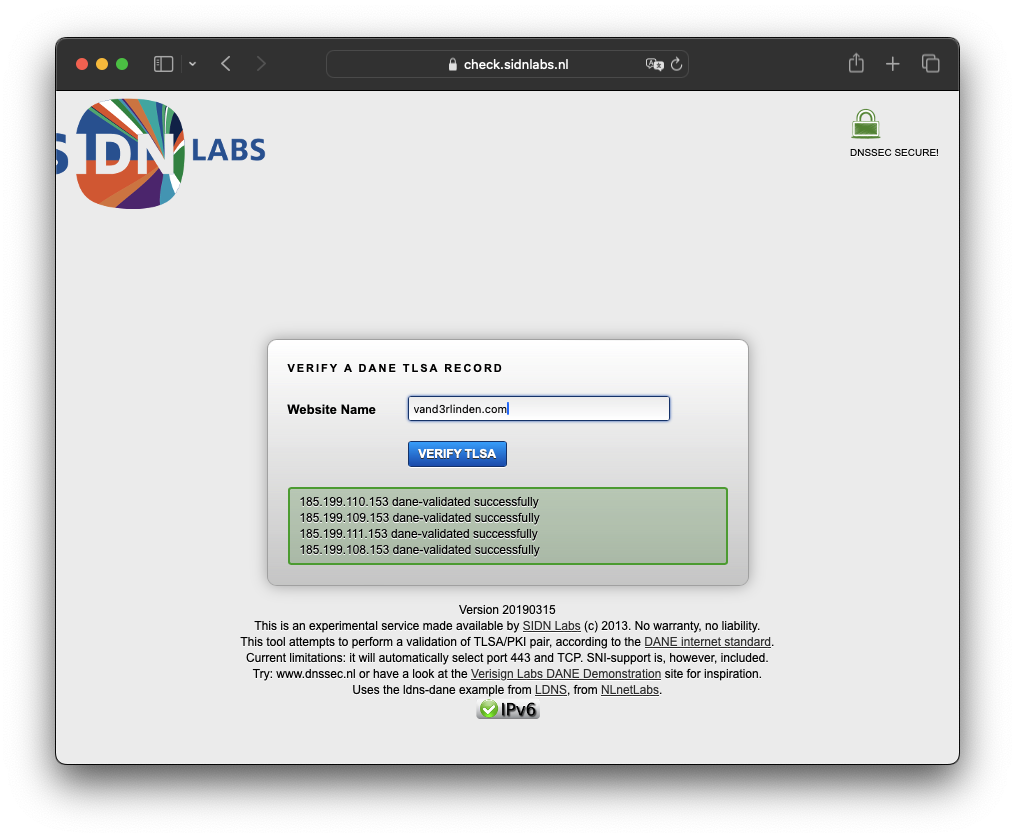 Source: https://check.sidnlabs.nl/dane/
Source: https://check.sidnlabs.nl/dane/
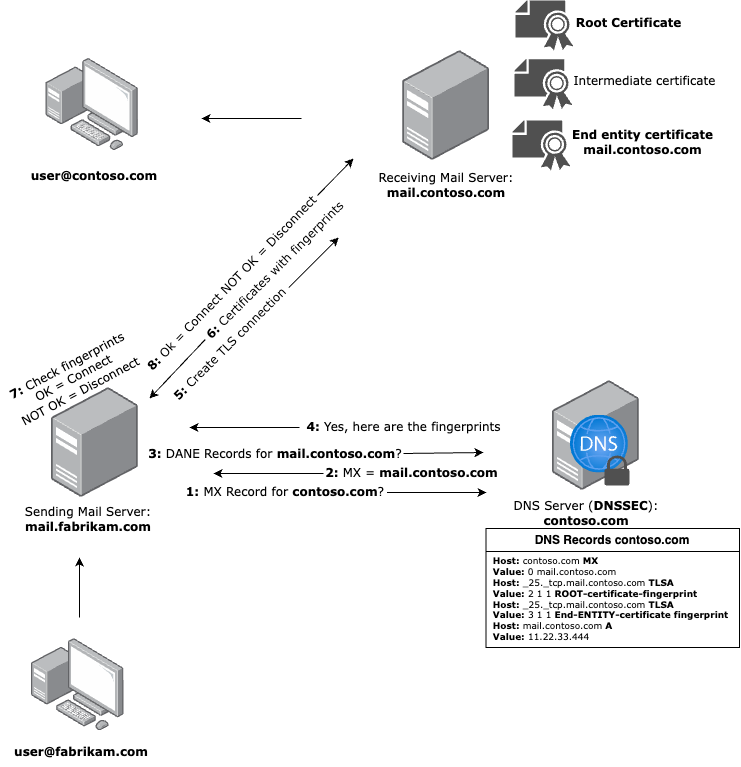
DNSSEC and DANE on a mailserver
SMTP DANE is a security protocol that uses DNSSEC to verify the authenticity of TLS certificates used for securing email communication. It helps protect against attacks such as TLS downgrade and man-in-the-middle attacks by ensuring that the certificates and encryption settings used in mail server communications are authentic and trustworthy.
While SPF, DKIM, and DMARC focus on verifying the authenticity of email messages and ensuring they are sent from authorized domains, SMTP DANE focuses specifically on securely establishing TLS connections between mail servers. By leveraging DNSSEC to publish certificate information directly in DNS, SMTP DANE ensures that the sending mail server connects to the intended receiving mail server with verified encryption, enhancing the overall security of email transport.
The flow of SMTP DANE on a mailserver
- Outbound SMTP DANE with DNSSEC
sending mail server: Requests DANETLSArecords of the receiving domain’sMXrecord. - Inbound SMTP DANE with DNSSEC
receiving mail server: Requires DNSSEC and DANETLSArecords that can be requested by the sending mail server.
To Summarize
The use of DNSSEC and DANE is critical to strengthening online security. DNSSEC ensures data integrity and authentication in the DNS, while DANE associates digital certificates with domain names to prevent unauthorized access. Together, they form a powerful defense against evolving cyber threats, promoting trust and improving overall Internet security.
