Safe Links scans URLs in incoming messages and checks the links for malicious content at the time they are clicked.
What you can manage with a Safe Links policy
With a Safe Links policy, administrators can configure and manage this policy to protect users from clicking harmful links and being redirected to malicious websites. Safe Links provides URL scanning for links in email messages, Microsoft Teams, and supported Office 365 applications. You can create custom Safe Links policies that apply to specific users, groups, or domains.
Although there’s no default policy for Safe Links, the Built-in protection preset security policy provides Safe Links protection for all recipients by default (users who aren’t defined in the Standard or Strict preset security policies or in custom Safe Links policies).
Safe Links protection through Safe Links policies is accessible in the following locations:
-
Email messages:
- Safe Links protection for links embedded in email messages.
-
Microsoft Teams:
- Safe Links protection for links within Teams conversations, group chats, or originating from channels.
-
Office apps:
- Safe Links protection for supported Office desktop, mobile, and web applications.
Safe Links policy configuration
You configure Safe Links policies in the Microsoft Security portal or in Exchange Online PowerShell with the New-SafeLinksPolicy cmdlet.
In this article, we will use the Microsoft Security portal for the configuration.
-
Go to the Safe links Policies in the Microsoft Security portal.
-
Click on ‘Create’.
-
Specify a policy name such as
TENANTSHORT - Safe links policy. -
Under ‘Users and Domains’, select the users, groups, and/or domains you want to include (In my case, I configured all the accepted domains).
- If desired, exclude groups such as Microsoft 365 groups or mail-enabled security groups.
-
Under ‘URL & click protection settings’ you can set your URL and click protection settings for Email, Teams and Office 365 Apps
-
Email:
-
Safe Links checks a list of known, malicious links when users click links in email. URLs are rewritten by default (recommended value:
$true). -
Apply Safe Links to email messages sent within the organization (recommended value:
$true). -
Apply real-time URL scanning for suspicious links and links that point to files (recommended value:
$true). -
Wait for URL scanning to complete before delivering the message (recommended value:
$true). -
Do not rewrite URLs, do checks via Safe Links API only (recommended value:
$false).- Wrapping URLs (Do not rewrite URLs:
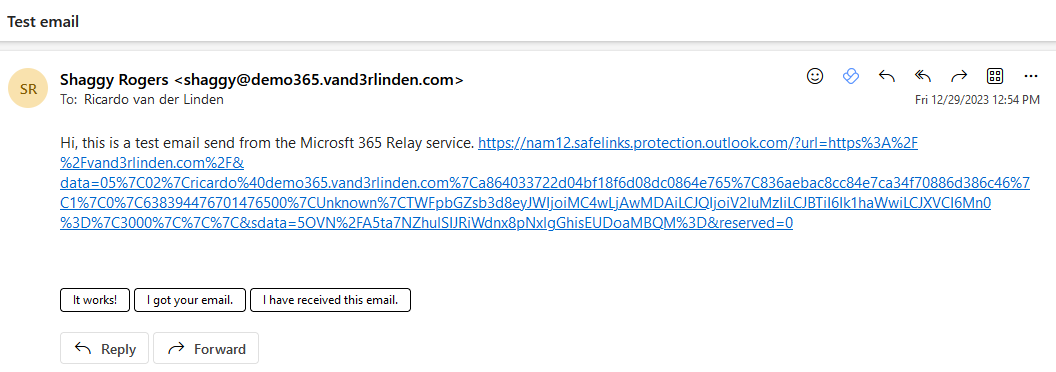
$false) ensures more consistent protection across all email clients, while disabling it (Do not rewrite URLs$true) offers a cleaner experience but limits protection to supported Outlook clients only. Below a summary table:- URL Wrapping (Do not rewrite URLs:
$false)- URLs are rewritten into a
safelinks.protection.outlook.comformat. - Protection happens at click-time, using Microsoft’s backend to evaluate the link.
- Works across all clients, even those that don’t support Safe Links APIs (e.g., mobile apps, third-party email apps).
- Microsoft recommends it for environments where users access emails from a variety of clients and devices.
- URLs are rewritten into a
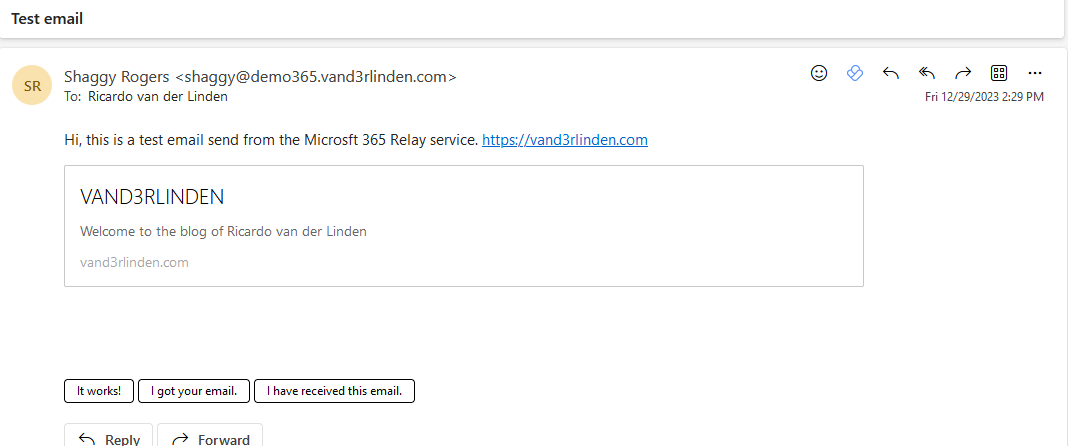
- No URL Rewriting (Do not rewrite URLs:
$true)- URLs remain in their original form; they are not visibly changed.
- Scanned before delivery, and checked again at click-time using Safe Links APIs.
- Only supported in modern Outlook clients: Outlook for Windows, Mac, and Outlook on the web (OWA).
- Cleaner experience (no strange-looking links), but less coverage, older clients or unsupported apps won’t trigger click-time protection.
- URL Wrapping (Do not rewrite URLs:
- Wrapping URLs (Do not rewrite URLs:
-
Do not rewrite the following URLs in email (recommended value:
none).- URLs in the “Don’t rewrite the following URLs” list bypass Safe Links scanning. Report it as “Should not have been blocked (False positive)” and choose “Allow this URL” to prevent Safe Links from scanning during mail flow and at the time of click. This adds the URL to the Tenant Allow/Block List.
- Instruction: Report good URLs to Microsoft
- URLs in the “Don’t rewrite the following URLs” list bypass Safe Links scanning. Report it as “Should not have been blocked (False positive)” and choose “Allow this URL” to prevent Safe Links from scanning during mail flow and at the time of click. This adds the URL to the Tenant Allow/Block List.
-
Rewrite URLs example:
-
Do not rewrite URLs example:
-
-
Teams:
- Safe Links checks a list of known, malicious links when users click links in Microsoft Teams. URLs are not rewritten (recommended value:
$true).- This setting may require up to 24 hours to become effective. It influences the functionality of time-of-click protection.
- Safe Links checks a list of known, malicious links when users click links in Microsoft Teams. URLs are not rewritten (recommended value:
-
Office 365 apps:
- Safe Links checks a list of known, malicious links when users click links in Microsoft Office apps. URLs are not rewritten (recommended value:
$true).- Safe Links is supported in Office 365 desktop and mobile (iOS and Android) apps.
- Safe Links checks a list of known, malicious links when users click links in Microsoft Office apps. URLs are not rewritten (recommended value:
-
Click protection settings:
- Track user clicks (recommended value:
$true) - Let users click through to the original URL (recommended value:
$false).- This disables the option to prevent users from clicking through to the original URL in warning pages.
- Display the organization branding on notification and warning pages (recommended value:
none).
- Track user clicks (recommended value:
-
Notification:
- Use custom notification text (recommended value:
none).
- Use custom notification text (recommended value:
-
-
Save your new Safe links policy
NOTE: Allow up to 6 hours for a new or updated policy to be applied.
