False positives block important emails, while false negatives allow harmful ones through. Learn how to manage these emails effectively in Microsoft Defender for Office 365.
How inbound email works in Microsoft 365
To understand why your environment experiences false positives and false negatives, you first need to understand how Microsoft 365 handles inbound email.
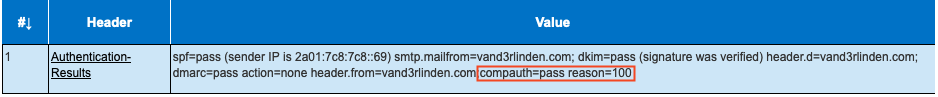
Microsoft 365 uses implicit email authentication to determine the final verdict for inbound messages. This approach goes beyond traditional SPF, DKIM, and DMARC checks by incorporating additional signals to evaluate inbound email. By leveraging these extra signals, emails that would typically fail standard authentication can pass implicit authentication and be successfully delivered to Microsoft 365.
These signals include:
- Sender reputation
- Sender history
- Recipient history
- Behavioral analysis
The results of Microsoft’s implicit authentication checks are combined into a single value called composite authentication (compauth). This value is stamped into the Authentication-Results message header.
False positives and False negatives
- False Positive (
FP): is when an email isn’t actually spam, but your system mistakenly thinks it is and puts it in the spam or quarantine folder. - False Negative (
FN): happens when an email is actually spam, but your system mistakenly lets it through, thinking it’s not spam.
Sometimes the signals of the implicit authentication gets it wrong, and therefore a good message can be a flagged as a bad one (false positive) and a questionable email message can be get through (false negative).
NOTE: Implicit authentication helps prevent the rejection of legitimate emails that may, for example, fail DMARC checks during inbound processing. If you’re looking for more granular control over how DMARC failures are handled, this blog post is worth reading.
To help these signals to get better you can report good emails as False Positive or report questionable emails as False Negative to Microsoft using the Report Submission page.
Handling false positives
Once you report a false positive (good email), you can, if desired, create an allow entry in the Tenant Allow/Block List for domains, email addresses, files, and URLs.
These entries are retained for 45 days after the filtering system determines that the entity is clean, and then the allow entry is removed. For example: If you create an allow entry on July 1 with removal set for 45 days after the last use, and the entity is deemed malicious until July 29 but clean from July 30, the last used date updates until July 29. Since it’s clean, updates stop on July 30, and the entry is removed on September 12 (45 days after the last update).
NOTE: You cannot report IP addresses through the Submissions page, but you can manually create an allow entry in the Tenant Allow/Block List. Note that only IPv6 addresses are supported, IPv4 addresses are not.
In addition to implicit authentication checks, you can also reduce false positives by disabling the ASF (Advanced Spam Filter) settings in your Anti-spam inbound policy, as enabling one or more ASF settings is an aggressive approach to spam filtering that often results in false positives. For example, messages containing certain elements may be marked as spam or have their spam score increased. Additionally, messages filtered by ASF cannot be reported to Microsoft as false positives.
Handling false negatives
Once you report a false negative (questionable email), you can, if desired, create a block entry in the Tenant Allow/Block List for domains and email addresses, files and URLs.
These entries expire after 30 days, but you can also set them to expire after 90 days or never. Block entries for spoofed senders and IP addresses never expire.
NOTE: You cannot report IP addresses through the Submissions page, but you can manually create a block entry in the Tenant Allow/Block List. Note that only IPv6 addresses are supported, IPv4 addresses are not.
In addition to the implicit authentication checks and the recommended anti-phishing and anti-spam techniques provided by MDO, end users should remain vigilant by identifying red flags in email messages, such as carefully reviewing the sender address, subject line, and message content.
To give end users more red flags to look for when they receive an email message, the following can be used or implemented:
You must also allow users to report false negatives (questionable emails) and false positives (good emails) to Microsoft by enabling the built-in Report button, if you haven’t already done so, or by using a third-party solution such as KnowBe4.
NOTE: If you are still using the Microsoft Report Message or Report Phishing add-ins, consider transitioning to the built-in report button. These add-ins have security vulnerabilities that make them unsafe for your organization and will be deprecated over time.
Finally, end users can be educated with a security awareness program to help them recognize questionable emails. See also this blog post.
