This blog post explains how an MTA-STS policy works and how to implement it on GitHub Pages.
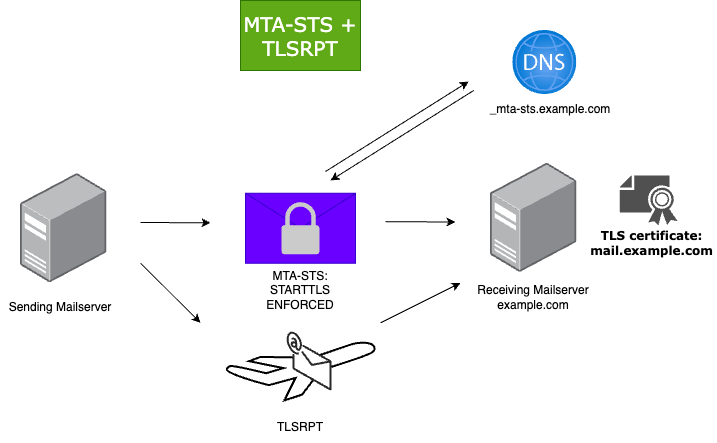
MTA-STS (Mail Transfer Agent Strict Transport Security) is a transport security mechanism (TLS enforcement) that protects SMTP delivery, it allows a sending (outbound) mail server to enforce the use of TLS by retrieving a secured HTTPS policy file published by the domain of the receiving (inbound) mail server. When MTA-STS is in enforce mode, the sending (outbound) mail server must validate that the receiving (inbound) mail server’s TLS certificate is valid, trusted, and matches the domain (the domain name in the TLS certificate must match the MX record of the domain).
Since port 25 does not use authentication (MTA-to-MTA delivery), implementing an MTA-STS policy enforces TLS encryption and certificate validation between MTA’s, this ensures the confidentiality of email delivery.
How MTA-STS Works
-
Discovery:
- When a sending mail server (MTA) wants to deliver an email to a domain, it first checks for the presence of the
_mta-sts.example.comDNS TXT record. - If the record exists, the sending server retrieves the policy file from
https://mta-sts.example.com/.well-known/mta-sts.txt.
- When a sending mail server (MTA) wants to deliver an email to a domain, it first checks for the presence of the
-
Policy Evaluation:
- The sending server reads the policy file and checks the mode (
enforce,testing, ornone). - If the mode is
enforce, the sending server must use TLS and verify the certificate of the receiving server (mail.example.com).
- The sending server reads the policy file and checks the mode (
-
TLS Reporting (TLSRPT)
- If the sending mail server encounters issues delivering an email, it can use the receiving server’s
TLSRPTrecord to report the problem or confirm that the TLS session was successfully established.
- If the sending mail server encounters issues delivering an email, it can use the receiving server’s
MTA-STS benefits:
- Emails are transfered over a secure TLS connection
- Must use TLS-Version 1.2 or higher
- For the TLS certificates they need to:
- Certificate subject needs to match the MX-Entry
- They need to be signed and issued by a public trusthworthy CA
- They need to be valid (valid from / valid until)
MTA-STS consists of:
- MTA STS DNS TXT Record (
_mta-sts.example.com) - MTA-STS Policy on
HTTPS(https://mta-sts.example.com/.well-known/mta-sts.txt)- A valid TLS certificate is required to be in place for
mta-sts.example.com
- A valid TLS certificate is required to be in place for
- SMTP TLS Reporting DNS TXT Record (
_smtp._tls.example.com)
Implement an MTA-STS policy for a domain
1: Add a DNS TXT record for the MTA STS policy
This TXT record is placed at _mta-sts.example.com and signals the presence of an MTA-STS policy.
_mta-sts.example.com IN TXT "v=STSv1; id=20240728"
v=STSv1:Indicates the version of the MTA-STS policy.id=2024072801: A unique identifier for the policy. This can be a date-based identifier or any other unique string. It must be updated whenever the policy file is changed.
2: Host the MTA-STS Policy file (in this blog we use Github Pages)
- Create a new public repository called
mta-sts - Disabling Jekyll, GitHub Pages is powered by Jekyll, a static website generator. However, Jekyll does not serve folders that begin with a dot. In order to do so, we’ll add a single empty file called
.nojekyllto the repo. - Creating the MTA-STS Policy in
.well-known/mta-sts.txtwith the following content, and make sure to list all MX records for your domain:
version: STSv1
mode: testing
mx: mail.example.com
mx: secondmx.example.com
max_age: 604800
NOTE: To find your MX record(s), you can check your public DNS or use a tool like dig, and run:
dig example.com MX +short
-
Activating GitHub Pages for the subdomain:
mta-sts- Go to your DNS provider and add a
CNAMErecord with the following details:
Host: mta-sts.example.com Value: github-username.github.io.- After adding the record, return to your GitHub repository, click Settings in the repository navigation, and scroll down to Pages.
- Under Build and deployment, change the Branch to be the
mainand selectrootas the publishing folder. Click Save, this will activate Github pages. - Under Custom domain add
mta-sts.example.com, this will create a commit that adds aCNAMEfile directly to the root of your repository.
- Under Build and deployment, change the Branch to be the
- Go to your DNS provider and add a
-
Once your custom domain is set up, GitHub will begin the process of issuing an SSL certificate using Let’s Encrypt. This process typically takes around 15 minutes but can take up to 24 hours. Once the certificate is issued, the Enforce HTTPS checkbox will be clickable. After enabling this setting, the policy is deployed. You can verify this by navigating to:
https://mta-sts.example.com/.well-known/mta-sts.txt- you should see the policy, and it should have loaded overHTTPS.
Example:
- MTA-STS policy for
vand3rlinden.com: https://mta-sts.vand3rlinden.com/.well-known/mta-sts.txt - Repository of the MTA-STS policy for
mta-sts.vand3rlinden.com: https://github.com/vand3rlinden/mta-sts
2.1: Detailed Explanation of the Policy File
version: STSv1: Indicates the version of the MTA-STS policy.mode: enforce: Specifies that the policy should be strictly enforced. Other modes aretesting(send report only) andnone(do nothing).mx: Lists each of the MX servers that handle email for your domain. If needed, wildcards are allowd, such as*.j-v1.mx.microsoftmax_age: 604800: Specifies the duration (in seconds) that the policy is valid. After this time, the sending MTA should refresh the policy.- The time (in seconds) that a sending MTA is allowed to cache the policy. The minimum recommended value is 1 week (604800 seconds).
In the
mta-sts.txtfile, you should list all MX servers that are used for receiving (inbound) emails for your domain and that support TLS.
2.2: From testing to enforce
- Start with Testing Mode: It is advisable to start with the
testingmode. This allows you to monitor and log the results (with TLS reporting) without affecting email delivery. It helps you ensure that your MX servers are correctly configured to support TLS before enforcing the policy. - Transition to Enforce Mode: Once you are confident that your MX servers support TLS and that email can be securely delivered, you can switch to
enforcemode to enhance your email security.
3: Activate TLS Reporting (TLSRPT)
TLS Reporting (TLSRPT) is a standard that provides a way to report when the TLS connection could not be established during email transmission.
3.1: Implementation of TLSRPT
- Log in to your DNS hosting provider’s management console.
- Add a new TXT record with the following details:
| Host | Type | Value |
|---|---|---|
_smtp._tls.example.com |
TXT |
v=TLSRPTv1; rua=mailto:tlsrpt@example.com |
3.2: TLSRPT report handling
If a sending mail server has issues securely delivering email to a receiving mail server, it can use the TLSRPT record published in the public DNS of the receiving domain to determine where to send a report about the problem or to report a successful TLS session.
The reports are received in .json, you can look for the summary tag to check if the TLS connection was failed or successful:
"summary":{"total-successful-session-count":1,"total-failure-session-count":0}
MTA-STS vs. SMTP DANE
Neither SMTP DANE nor MTA-STS is universally better. SMTP DANE provides stronger security, but requires DNSSEC, and not every DNS provider supports DNSSEC yet. MTA-STS is easier to implement and provides good security through HTTPS and DNS. Using the two together can provide the best of both worlds, increasing security through a layered approach.
This layered approach can be beneficial because MTA-STS enforces TLS through a secure HTTPS policy file and validates the TLS certificate of the receiving (inbound) mail server, while SMTP DANE provides similar protection by retrieving TLS fingerprints from the TLSA records from the MX host of the receiving domain and comparing them with the fingerprints presented by the receiving (inbound) mail server of the receiving domain.
MTA-STS and SMTP DANE vs. Outbound email authentication
While SPF, DKIM, and DMARC focus on verifying the authenticity of email messages and ensuring they are sent from authorized domains for outbound email, SMTP DANE and MTA-STS focuses specifically on securely establishing TLS connections between mail servers. These protocols ensures that the sending mail server connects to the intended receiving inbound mail server with verified encryption.
