Quarantine policies let you control the quarantine on how users can use it. This post will cover the default policies and how to create a custom policy.
What are quarantine policies
Back in April 2020, Microsoft made it possible for users to view, release, or delete quarantined messages (expect high confidence phishing). Some organizations were not happy about users having access to their own quarantined items. Quarantine policies give you more control over the quarantine for your end users and allow you to decide which quarantined items they are allowed to release.
The default quarantine policies
You can access it from the Quarantine policies section in Microsoft Defender XDR.
Out of the box, you will see three policies:
- DefaultFullAccessPolicy
- AdminOnlyAccessPolicy
- DefaultFullAccessWithNotificationPolicy
DefaultFullAccessPolicy
This policy has the quarantine settings as we have them since April 2020, and includes the following settings (expect high confidence phishing):
User message access:
- release the message from quarantine
- block sender (Outlook block sender list, junk mail settings)
- delete the message
- preview the message
Quarantine notification:
- Disabled
AdminOnlyAccessPolicy
This policy is the default High Confidence Phishing (HSPM) policy and assigns no access permissions to the items, and includes the following settings:
User message access:
- No allowed actions
Quarantine notification:
- Disabled
DefaultFullAccessWithNotificationPolicy
This policy has the same settings as the DefaultFullAccessPolicy quarantine policy, but with quarantine notifications enabled, and includes the following settings:
User message access:
- release the message from quarantine
- block sender (Outlook block sender list, junk mail settings)
- delete the message
- preview the message
Quarantine notification:
- Enabled
Create a custom quarantine policy, such as for request to release
In some situations, you may want your users to be able to request that a message be released from quarantine, rather than releasing it themselves. To do this, you can create a custom quarantine policy by following the steps below:
- Go to Quarantine Policies in Microsoft Defender XDR.
- Click on ‘Add custom policy’.
- Specify a policy name such as DefaultRequestAccessWithNotificationPolicy.
- Under Recipient Message Access select Limited access.
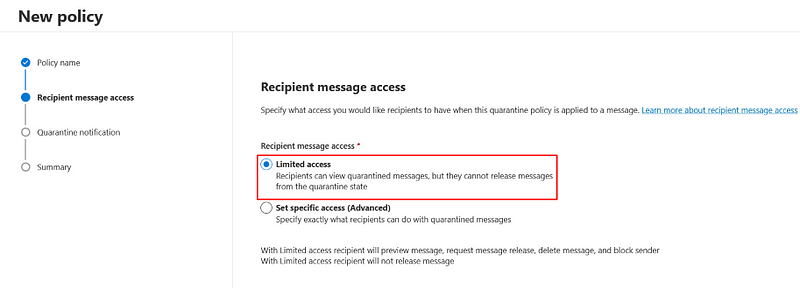
With Set specific access you can turn on or off each User message access action as desired, for more advanced configurations.
- Enable quarantine notifications, if desired.
- Safe your policy.
Outcome:
The User message access actions for the created custom quarantine policy will be:
- request to release the message from quarantine
- block sender (Outlook block sender list, junk mail settings)
- delete the message
- preview the message
Quarantine notification:
- Enabled
Users can request release of quarantined items after you assign the quarantine policy to an action in one of the threat policies, as described above:
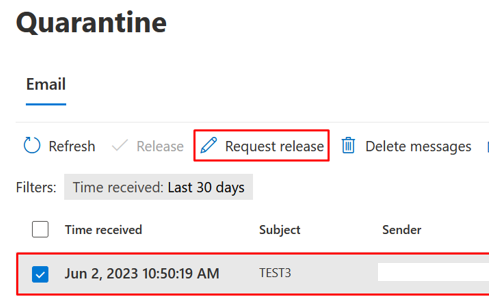
Tenant Admins (Entra permissions Global Administrator or Security Administrator) or Quarantine Administrators (Defender Portal permissions) can approve or deny release requests in the quarantine:
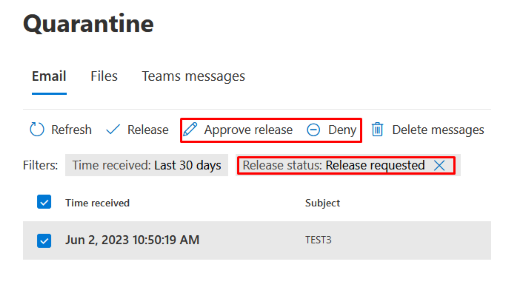
NOTE: Users cannot release their own quarantined messages in the following situations, regardless of how the quarantine policy is configured: Messages quarantined as malware by anti-malware policies, Messages quarantined as malware or phishing by Safe Attachments policies and Messages quarantined as high confidence phishing by anti-spam policies.
Quarantine Administrators in the Defender Portal
Quarantine Administrators is an Email & Collaboration role group in Microsoft Defender XDR. If XDR Unified role-based access control (RBAC) is enabled, grant the permissions Security operations/Security Data/Email & collaboration quarantine (manage) within the Microsoft Defender XDR Unified RBAC Portal.
To ensure Quarantine Administrators are notified of release requests, add them as recipients in the ‘User requested to release a quarantined message’ alert policy. This will send them an informational email alert whenever a user requests a release from quarantine.
Global settings
You can also change the notification email settings under Global Settings, where you can set settings such as the recurrence of quarantine notifications or change the layout of the email.
In summary
After you have set up the quarantine policies the way you want them, you can use your quarantine policies in the threat policies actions.
